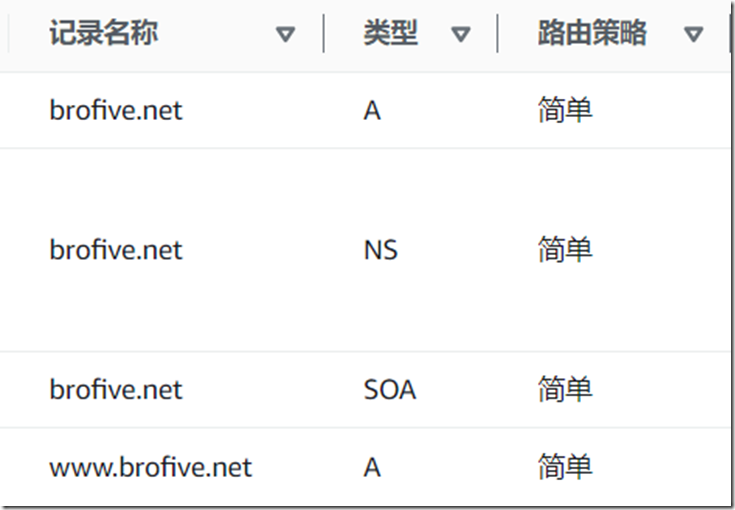
此前一直使用Godaddy的域名服务器,但是几年后失效了,再想使用的时候,发现Godaddy被墙了,而且价格也变成39欧元/年,这个就有些敲竹杠了。于是就申请国内的域名服务,才知道为啥网上一片差评,真是谁申请谁知道!然后就尝试了一下AWS域名服务器,这个域名服务就是著名的Route53!Route53是一个内外统一管理的域名服务,既可以单独申请互联网域名,也可使当做托管在AWS的业务系统的内部域名服务;既可以新申请互联网域名,也可以导入托管在其他域名服务商的域名(需存在合作)。一个域名的价格根据流行程度定价,例如com就比net贵,vip就比top贵。新申请brofive.net域名,每年服务费11$。AWS的域名服务功能很多,远比Godaddy强!高级配置功能对于复杂的网站群应该很有用处,但是对于个人网站帮助不大,提供企业级功能是获取大型客户的关键!
然后就折腾配置域名,好久不用有些生疏,且Route53的功能太多了,眼花缭乱!看了AWS的手册,才算弄明白怎么开始配置,需要新建托管区域,初次配置等待生效需要好久,上午起来一看,终于生效了,可以用站长工具查看(https://uutool.cn/nslookup/)。有些细节配置不对,修改了一些参数,然后手工配置Wordexpress里面的数据库的wp_options表,这下就可以访问了!有些事情原理很简单,自己能用好,还是有很多细节!
下面是一些关于域名DNS的常识科普,AWS支持13种记录类型,AWSRoute53配置手册,没有去查RFC,估计也差不多都支持了!
Route 53 provides an extension to DNS functionality known as alias records. Similar to CNAME records, alias records let you route traffic to selected AWS resources, such as CloudFront distributions and Amazon S3 buckets. For more information, including a comparison of alias and CNAME records, see Choosing between alias and non-alias records.
Topics
- A record type
- AAAA record type
- CAA record type
- CNAME record type
- DS record type
- MX record type
- NAPTR record type
- NS record type
- PTR record type
- SOA record type
- SPF record type
- SRV record type
- TXT record type
A record type
<?XML:NAMESPACE PREFIX = “[default] http://www.w3.org/2000/svg” NS = “http://www.w3.org/2000/svg” />
You use an A record to route traffic to a resource, such as a web server, using an IPv4 address in dotted decimal notation.
Example for the Amazon Route 53 console
192.0.2.1
Example for the Route 53 API
<Value>192.0.2.1</Value>
AAAA record type
You use an AAAA record to route traffic to a resource, such as a web server, using an IPv6 address in colon-separated hexadecimal format.
Example for the Amazon Route 53 console
2001:0db8:85a3:0:0:8a2e:0370:7334
Example for the Route 53 API
<Value>2001:0db8:85a3:0:0:8a2e:0370:7334</Value>
CAA record type
A CAA record specifies which certificate authorities (CAs) are allowed to issue certificates for a domain or subdomain. Creating a CAA record helps to prevent the wrong CAs from issuing certificates for your domains. A CAA record isn’t a substitute for the security requirements that are specified by your certificate authority, such as the requirement to validate that you’re the owner of a domain.
You can use CAA records to specify the following:
- Which certificate authorities (CAs) can issue SSL/TLS certificates, if any
- The email address or URL to contact when a CA issues a certificate for the domain or subdomain
When you add a CAA record to your hosted zone, you specify three settings separated by spaces:
flags tag "value"
Note the following about the format for CAA records:
- The value of
tagcan contain only the characters A-Z, a-z, and 0-9. - Always enclose
valuein quotation marks (“”). - Some CAs allow or require additional values for
value. Specify additional values as name-value pairs, and separate them with semicolons (;), for example:0 issue "ca.example.net; account=123456" - If a CA receives a request for a certificate for a subdomain (such as www.example.com) and if no CAA record for the subdomain exists, the CA submits a DNS query for a CAA record for the parent domain (such as example.com). If a record for the parent domain exists and if the certificate request is valid, the CA issues the certificate for the subdomain.
- We recommend that you consult with your CA to determine what values to specify for a CAA record.
- You can’t create a CAA record and a CNAME record that have the same name because DNS doesn’t allow using the same name for both a CNAME record and any other type of record.
Topics
- Authorize a CA to issue a certificate for a domain or subdomain
- Authorize a CA to issue a wildcard certificate for a domain or subdomain
- Prevent any CA from issuing a certificate for a domain or subdomain
- Request that any CA contacts you if the CA receives an invalid certificate request
- Use another setting that is supported by the CA
- Examples
Authorize a CA to issue a certificate for a domain or subdomain
To authorize a CA to issue a certificate for a domain or subdomain, create a record that has the same name as the domain or subdomain, and specify the following settings:
- flags –
0 - tag –
issue - value – the code for the CA that you authorize to issue a certificate for the domain or subdomain
For example, suppose you want to authorize ca.example.net to issue a certificate for example.com. You create a CAA record for example.com with the following settings:
0 issue "ca.example.net"
For information about how to authorize AWS Certificate Manager to issue a certificate, see Configure a CAA record in the AWS Certificate Manager User Guide.
Authorize a CA to issue a wildcard certificate for a domain or subdomain
To authorize a CA to issue a wildcard certificate for a domain or subdomain, create a record that has the same name as the domain or subdomain, and specify the following settings. A wildcard certificate applies to the domain or subdomain and all of its subdomains.
- flags –
0 - tag –
issuewild - value – the code for the CA that you authorize to issue a certificate for a domain or subdomain, and its subdomains
For example, suppose you want to authorize ca.example.net to issue a wildcard certificate for example.com, which applies to example.com and all of its subdomains. You create a CAA record for example.com with the following settings:
0 issuewild "ca.example.net"
When you want to authorize a CA to issue a wildcard certificate for a domain or subdomain, create a record that has the same name as the domain or subdomain, and specify the following settings. A wildcard certificate applies to the domain or subdomain and all of its subdomains.
Prevent any CA from issuing a certificate for a domain or subdomain
To prevent any CA from issuing a certificate for a domain or subdomain, create a record that has the same name as the domain or subdomain, and specify the following settings:
- flags –
0 - tag –
issue - value –
";"
For example, suppose you don’t want any CA to issue a certificate for example.com. You create a CAA record for example.com with the following settings:
0 issue ";"
If you don’t want any CA to issue a certificate for example.com or its subdomains, you create a CAA record for example.com with the following settings:
0 issuewild ";"
Note
If you create a CAA record for example.com and specify both of the following values, a CA that is using the value ca.example.net can issue the certificate for example.com:
0 issue ";"
0 issue "ca.example.net"
Request that any CA contacts you if the CA receives an invalid certificate request
If you want any CA that receives an invalid request for a certificate to contact you, specify the following settings:
- flags –
0 - tag –
iodef - value – the URL or email address that you want the CA to notify if the CA receives an invalid request for a certificate. Use the applicable format:
"mailto:email-address""http://URL""https://URL"
For example, if you want any CA that receives an invalid request for a certificate to send email to admin@example.com, you create a CAA record with the following settings:
0 iodef "mailto:admin@example.com"
Use another setting that is supported by the CA
If your CA supports a feature that isn’t defined in the RFC for CAA records, specify the following settings:
- flags – 128 (This value prevents the CA from issuing a certificate if the CA doesn’t support the specified feature.)
- tag – the tag that you authorize the CA to use
- value – the value that corresponds with the value of tag
For example, suppose your CA supports sending a text message if the CA receives an invalid certificate request. (We aren’t aware of any CAs that support this option.) Settings for the record might be the following:
128 exampletag "15555551212"
Examples
Example for the Route 53 console
0 issue "ca.example.net"
0 iodef "mailto:admin@example.com"
Example for the Route 53 API
<ResourceRecord>
<Value>0 issue "ca.example.net"</Value>
<Value>0 iodef "mailto:admin@example.com"</Value>
</ResourceRecord>
CNAME record type
A CNAME record maps DNS queries for the name of the current record, such as acme.example.com, to another domain (example.com or example.net) or subdomain (acme.example.com or zenith.example.org).
Important
The DNS protocol does not allow you to create a CNAME record for the top node of a DNS namespace, also known as the zone apex. For example, if you register the DNS name example.com, the zone apex is example.com. You cannot create a CNAME record for example.com, but you can create CNAME records for www.example.com, newproduct.example.com, and so on.
In addition, if you create a CNAME record for a subdomain, you cannot create any other records for that subdomain. For example, if you create a CNAME for www.example.com, you cannot create any other records for which the value of the Name field is www.example.com.
Amazon Route 53 also supports alias records, which allow you to route queries to selected AWS resources, such as CloudFront distributions and Amazon S3 buckets. Aliases are similar in some ways to the CNAME record type; however, you can create an alias for the zone apex. For more information, see Choosing between alias and non-alias records.
Example for the Route 53 console
hostname.example.com
Example for the Route 53 API
<Value>hostname.example.com</Value>
DS record type
A delegation signer (DS) record refers a zone key for a delegated subdomain zone. You might create a DS record when you establish a chain of trust when you configure DNSSEC signing. For more information about configuring DNSSEC in Route 53, see Configuring DNSSEC signing in Amazon Route 53.
The first three values are decimal numbers representing the key tag, algorithm, and digest type. The fourth value is the digest of the zone key. For more information about the DS record format, see RFC 4034.
Example for the Route 53 console
123 4 5 1234567890abcdef1234567890absdef
Example for the Route 53 API
<Value>123 4 5 1234567890abcdef1234567890absdef</Value>
MX record type
An MX record specifies the names of your mail servers and, if you have two or more mail servers, the priority order. Each value for an MX record contains two values, priority and domain name.
- Priority
An integer that represents the priority for an email server. If you specify only one server, the priority can be any integer between 0 and 65535. If you specify multiple servers, the value that you specify for the priority indicates which email server you want email to be routed to first, second, and so on. The server with the lowest value for the priority takes precedence. For example, if you have two email servers and you specify values of 10 and 20 for the priority, email always goes to the server with a priority of 10 unless it’s unavailable. If you specify values of 10 and 10, email is routed to the two servers approximately equally.
Domain name
The domain name of the email server. Specify the name (such as mail.example.com) of an A or AAAA record. In RFC 2181, Clarifications to the DNS Specification, section 10.3 forbids specifying the name of a CNAME record for the domain name value. (When the RFC mentions “alias,” it means a CNAME record, not a Route 53 alias record.)
Example for the Amazon Route 53 console
10 mail.example.com
Example for the Route 53 API
<Value>10 mail.example.com</Value>
NAPTR record type
A Name Authority Pointer (NAPTR) is a type of record that is used by Dynamic Delegation Discovery System (DDDS) applications to convert one value to another or to replace one value with another. For example, one common use is to convert phone numbers into SIP URIs.
The Value element for an NAPTR record consists of six space-separated values:
- Order
- When you specify more than one record, the sequence that you want the DDDS application to evaluate records in. Valid values: 0-65535.
- Preference
- When you specify two or more records that have the same Order, your preference for the sequence that those records are evaluated in. For example, if two records have an Order of 1, the DDDS application first evaluates the record that has the lower Preference. Valid values: 0-65535.
- Flags
- A setting that is specific to DDDS applications. Values currently defined in RFC 3404 are uppercase- and lowercase letters “A”, “P”, “S”, and “U”, and the empty string, “”. Enclose Flags in quotation marks.
- Service
- A setting that is specific to DDDS applications. Enclose Service in quotation marks.
For more information, see the applicable RFCs:
- URI DDDS application – https://tools.ietf.org/html/rfc3404#section-4.4
- S-NAPTR DDDS application – https://tools.ietf.org/html/rfc3958#section-6.5
- U-NAPTR DDDS application – https://tools.ietf.org/html/rfc4848#section-4.5
- Regexp
- A regular expression that the DDDS application uses to convert an input value into an output value. For example, an IP phone system might use a regular expression to convert a phone number that is entered by a user into a SIP URI. Enclose Regexp in quotation marks. Specify either a value for Regexp or a value for Replacement, but not both.
The regular expression can include any of the following printable ASCII characters:
- a-z
- 0-9
- – (hyphen)
- (space)
- ! # $ % & ‘ ( ) * + , – / : ; < = > ? @ [ ] ^ _ ` { | } ~ .
- ” (quotation mark). To include a literal quote in a string, precede it with a \ character: \”.
- \ (backslash). To include a backslash in a string, precede it with a \ character: \\.
Specify all other values, such as internationalized domain names, in octal format.
For the syntax for Regexp, see RFC 3402, section 3.2, Substitution Expression Syntax
- Replacement
- The fully qualified domain name (FQDN) of the next domain name that you want the DDDS application to submit a DNS query for. The DDDS application replaces the input value with the value that you specify for Replacement, if any. Specify either a value for Regexp or a value for Replacement, but not both. If you specify a value for Regexp, specify a dot (.) for Replacement.
The domain name can include a-z, 0-9, and – (hyphen).
For more information about DDDS applications and about NAPTR records, see the following RFCs:
Example for the Amazon Route 53 console
100 50 "u" "E2U+sip" "!^(\\+441632960083)$!sip:\\1@example.com!" .
100 51 "u" "E2U+h323" "!^\\+441632960083$!h323:operator@example.com!" .
100 52 "u" "E2U+email:mailto" "!^.*$!mailto:info@example.com!" .
Example for the Route 53 API
<ResourceRecord>
<Value>100 50 "u" "E2U+sip" "!^(\\+441632960083)$!sip:\\1@example.com!" .</Value>
<Value>100 51 "u" "E2U+h323" "!^\\+441632960083$!h323:operator@example.com!" .</Value>
<Value>100 52 "u" "E2U+email:mailto" "!^.*$!mailto:info@example.com!" .</Value>
</ResourceRecord>
NS record type
An NS record identifies the name servers for the hosted zone. Note the following:
- The most common use for an NS record is to control how internet traffic is routed for a domain. To use the records in a hosted zone to route traffic for a domain, you update the domain registration settings to use the four name servers in the default NS record. (This is the NS record that has the same name as the hosted zone.)
- You can create a separate hosted zone for a subdomain (acme.example.com) and use that hosted zone to route internet traffic for the subdomain and its subdomains (subdomain.acme.example.com). You set up this configuration, known as “delegating responsibility for a subdomain to a hosted zone” by creating another NS record in the hosted zone for the root domain (example.com). For more information, see Routing traffic for subdomains.
- You also use NS records to configure white-label name servers. For more information, see Configuring white-label name servers.
For more information about NS records, see NS and SOA records that Amazon Route 53 creates for a public hosted zone.
Example for the Amazon Route 53 console
ns-1.example.com
Example for the Route 53 API
<Value>ns-1.example.com</Value>
PTR record type
A PTR record maps an IP address to the corresponding domain name.
Example for the Amazon Route 53 console
hostname.example.com
Example for the Route 53 API
<Value>hostname.example.com</Value>
SOA record type
A start of authority (SOA) record provides information about a domain and the corresponding Amazon Route 53 hosted zone. For information about the fields in an SOA record, see NS and SOA records that Amazon Route 53 creates for a public hosted zone.
Example for the Route 53 console
ns-2048.awsdns-64.net hostmaster.awsdns.com 1 1 1 1 60
Example for the Route 53 API
<Value>ns-2048.awsdns-64.net hostmaster.awsdns.com 1 1 1 1 60</Value>
SPF record type
SPF records were formerly used to verify the identity of the sender of email messages. However, we no longer recommend that you create records for which the record type is SPF. RFC 7208, Sender Policy Framework (SPF) for Authorizing Use of Domains in Email, Version 1, has been updated to say, “…[I]ts existence and mechanism defined in [RFC4408] have led to some interoperability issues. Accordingly, its use is no longer appropriate for SPF version 1; implementations are not to use it.” In RFC 7208, see section 14.1, The SPF DNS Record Type.
Instead of an SPF record, we recommend that you create a TXT record that contains the applicable value. For more information about valid values, see the Wikipedia article Sender Policy Framework.
Example for the Amazon Route 53 console
"v=spf1 ip4:192.168.0.1/16 -all"
Example for the Route 53 API
<Value>"v=spf1 ip4:192.168.0.1/16 -all"</Value>
SRV record type
An SRV record Value element consists of four space-separated values. The first three values are decimal numbers representing priority, weight, and port. The fourth value is a domain name. SRV records are used for accessing services, such as a service for email or communications. For information about SRV record format, refer to the documentation for the service that you want to connect to.
Example for the Amazon Route 53 console
10 5 80 hostname.example.com
Example for the Route 53 API
<Value>10 5 80 hostname.example.com</Value>
TXT record type
A TXT record contains one or more strings that are enclosed in double quotation marks ("). When you use the simple routing policy, include all values for a domain (example.com) or subdomain (www.example.com) in the same TXT record.
Topics
- Entering TXT record values
- Special characters in a TXT record value
- Uppercase and lowercase in a TXT record value
- Examples
Entering TXT record values
A single string can include up to 255 characters, including the following:
- a-z
- A-Z
- 0-9
- Space
- – (hyphen)
- ! ” # $ % & ‘ ( ) * + , – / : ; < = > ? @ [ \ ] ^ _ ` { | } ~ .
If you need to enter a value longer than 255 characters, break the value into strings of 255 characters or fewer, and enclose each string in double quotation marks ("). In the console, list all the strings on the same line:
"String 1" "String 2" "String 3"
For the API, include all the strings in the same Value element:
<Value>"String 1" "String 2" "String 3"</Value>
The maximum length of a value in a TXT record is 4,000 characters.
To enter more than one TXT value, enter one value per row.
Special characters in a TXT record value
If your TXT record contains any of the following characters, you must specify the characters by using escape codes in the format \three-digit octal code:
- Characters 000 to 040 octal (0 to 32 decimal, 0x00 to 0x20 hexadecimal)
- Characters 177 to 377 octal (127 to 255 decimal, 0x7F to 0xFF hexadecimal)
For example, if the value of your TXT record is "exämple.com", you specify "ex\344mple.com".
For a mapping between ASCII characters and octal codes, perform an internet search for “ascii octal codes.” One useful reference is ASCII Code – The extended ASCII table.
To include a quotation mark (") in a string, put a backslash (\) character before the quotation mark: \".
Uppercase and lowercase in a TXT record value
Case is preserved, so "Ab" and "aB" are different values.
Examples
Example for the Amazon Route 53 console
Put each value on a separate line:
"This string includes \"quotation marks\"."
"The last character in this string is an accented e specified in octal format: \351"
"v=spf1 ip4:192.168.0.1/16 -all"
Example for the Route 53 API
Put each value in a separate Value element:
<Value>"This string includes \"quotation marks\"."</Value>
<Value>"The last character in this string is an accented e specified in octal format: \351"</Value>
<Value>"v=spf1 ip4:192.168.0.1/16 -all"</Value>
相关信息: